The Rise of AI Coding Agents: Impact on Platform Engineering Teams
How AI coding agents like GitHub Copilot Workspace and Cursor are reshaping platform engineering. What teams need to prepare for and how to leverage these tools.
I thought identity would be the easy, boring part.
I’m building ProteinLens: a consumer-ish app today, with a clear path to “teams later” (B2B, SSO, enterprise domains). So I did what a reasonable Azure-native builder would do:
“Let’s implement Microsoft Entra External ID. It’s basically B2C 2.0, right? Social login now, SSO later. Done.”
Reader, it was not done.
What followed was authentication chaos: portals inside portals, concepts that sound identical but aren’t, and a sign-in experience that looks like I just teleported my users into someone else’s product.
This post is for anyone who wants the simplest thing:
…and is considering Entra External ID because “future enterprise”.
My mental model was:
In my head, it was the responsible choice.
In reality, it felt like adopting an entire identity platform when I just needed a door lock.
The moment you hit sign-in, you get a full redirect into a Microsoft-styled flow.
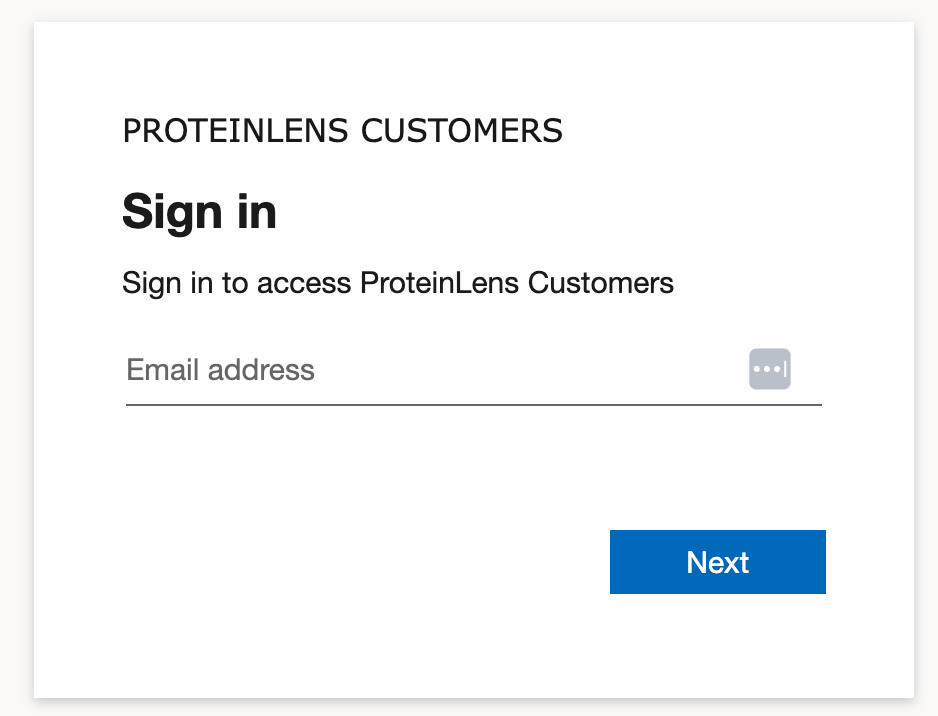
Even with branding, it’s still visibly “not my product”. The fonts, spacing, page layout, and interaction patterns don’t match. It breaks trust in a consumer app.
Yes, Microsoft Entra External ID supports “branding themes” for the hosted pages, but the customization has real limits (and it’s tenant-level theming, not a fully native embedded experience). (Microsoft Learn)
If you’re building something where conversion matters, this is not a small detail. Authentication is part of your product, not a compliance checkbox.
External ID has a lot of surface area:
None of that is “wrong” if you need it.
But if you’re shipping an MVP, it’s the identity equivalent of deploying Kubernetes to serve a static page.
I lost hours to the kind of friction that doesn’t show up in architecture diagrams:
It wasn’t hard in a fun way. It was hard in a paper-cut way.
I also hit the uncomfortable reality: Azure AD B2C is effectively closed to new customers.
Microsoft’s own FAQ states:
So if you’re a new product today and you thought “maybe I’ll just use classic B2C instead”… that door is basically closed.
That nudges you toward External ID—even when External ID is not the UX you want.
I looked at Clerk.
Clerk is slick and productive, and for many teams it’s exactly right. But my issue wasn’t “I want fewer lines of code.”
My issue was: I want a more seamless, product-native auth experience, and I want subscriptions + identity to feel cohesive.
Some auth tools feel like you’re renting someone else’s UI. Some feel like identity lego bricks. I want something that feels like it belongs to ProteinLens.
Here’s the brutally honest scope:
Everything else is optional until it’s not.
And when “it’s not” (B2B/SSO later), I want to add that without rebuilding the world.
I’m optimizing for shipping + UX + control, not “enterprise future-proofing” on day one.
A pragmatic approach that fits this stage:
Concretely, that usually means one of these patterns:
This is the “I want control” path.
Not all “hosted auth” is equal. Some tools allow deep theming or embedded components that truly match your UI; others will always feel like a redirect.
If redirect UX bothers you today, pick a provider that doesn’t force it.
This is the heresy take, but it’s often correct.
You don’t need SAML because you might have enterprise customers later. You need SAML because someone is ready to pay you for it.
Entra External ID is powerful. I can see it being the right choice for:
But for a consumer SaaS MVP where trust + flow + conversion matter?
The combination of:
…made it the wrong tool for my current stage.
So I’m going back to basics:
Own the experience. Keep auth simple. Integrate Stripe cleanly. Add SSO when it’s paid for.
AI & Cloud Advisor with 18+ years experience. Author of 8 technical books, creator of Ansible Pilot, and instructor at CopyPasteLearn Academy. Speaker at KubeCon EU & Red Hat Summit 2026.
How AI coding agents like GitHub Copilot Workspace and Cursor are reshaping platform engineering. What teams need to prepare for and how to leverage these tools.
Backstage is the de facto IDP. Adding AI makes it transformative — auto-generated docs, intelligent search, and self-service infrastructure. Here's the architecture.
Schedule Kubernetes workloads when and where the grid is greenest. How carbon-aware scheduling works, the tools available, and the business case for sustainable compute.